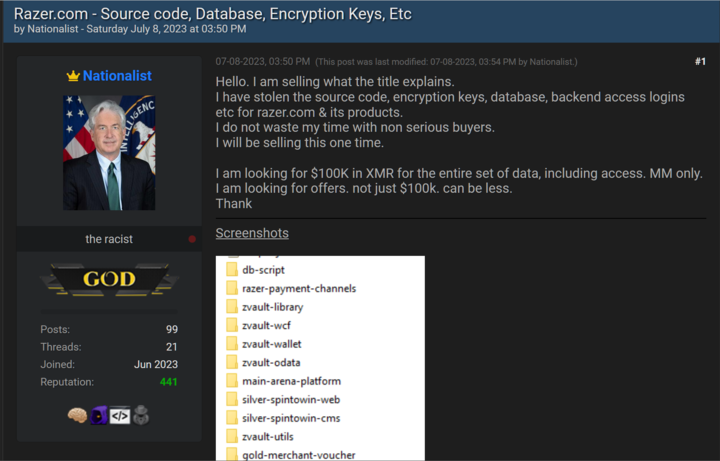
Cybersecurity Threats: A Real Concern for Your Operations
Let’s talk about a recent incident that shook the Los Angeles County Department of Health Services to its core. A phishing attack compromised the credentials of 23 employees, leading to the exposure of thousands of patients’ personal and health information. The aftermath of this breach serves as a stark reminder of the ever-present cybersecurity threats that can disrupt your operations and jeopardize sensitive data.
Understanding the Impact
Imagine the chaos that ensued when hackers gained access to patients’ personal and health data through compromised e-mail accounts. Names, dates of birth, contact details, medical records, and other sensitive information were at risk. While no Social Security Numbers or financial data were exposed, the breach still had far-reaching implications for both the affected individuals and the healthcare system.
The Importance of Reliable IT Support
In the face of such cybersecurity threats, having dependable IT support becomes non-negotiable. Daily infrastructure management, proactive security measures, and a comprehensive information security program are essential to safeguard your data and operations. Trust and accountability are paramount when choosing a provider to address your IT needs and compliance requirements.
Protecting Your Operations and Reputation
By investing in robust cybersecurity services, you can improve operational efficiency, enhance security measures, ensure compliance with industry standards, and focus more on your core operations. Avoiding downtime, mitigating IT-induced inefficiencies, and staying ahead of potential costs of non-compliance are key goals that can be achieved through a strategic approach to cybersecurity.
A Call to Action
As you navigate the complex landscape of IT management and cybersecurity threats, remember that staying safe online is a shared responsibility. We encourage you to explore ways to protect your organization from cyber threats, prioritize data security, and partner with trusted IT professionals to fortify your defenses. Let’s work together to safeguard your operations, enhance your security posture, and uphold the trust of your stakeholders.